I’m very excited to announce that I’ll be speaking on basic WordPress Security at WordCamp Albuquerque on January 19th, 2018.
This was a very busy week when it comes to hackers attacking WordPress websites. I talk to people about WordPress security best practices a lot, but most don’t want to hear it. They don’t think their little websites are significant enough to be attacked. After all, they aren’t an international law firm like Mossack Fonseca (MF) that keeps a lot of secrets. The MF data breach, aka the Panama Papers was the largest in history and revealed world-wide corruption at the highest levels. It was partially a WordPress hack on an old version of the Revolution Slider plugin. More recently (November 2017), the Paradise Papers appears to be a similar breach, although how the hack was accomplished is not yet clear. 40% of law firms who suffered data losses in 2016 apparently didn’t even know they had been breached. Now you may not run a high powered law firm with lots of secrets, but your digital assets, and more importantly your digital reputation (i.e. Google/Bing ranking) need to be protected. Forbes has an excellent article including steps you should take to protect your digital assets. The hackers simply don’t care how big you are, they just want your resources. Enough soap box…for now ;).
This week we had two significant security issues for WordPress that could affect quite a lot of us.
Brute Force Attacks by Botnet
A wide-spread brute force attack was reported by Wordfence where hackers are apparently using a single botnet to take control of compromised WordPress servers. These servers are then used to attack other WordPress websites and to mine the cryptocurrency, Monero. Wordfence gives a terrific forensic analysis of what they found. The gist of it is that the attacker has earned almost $100K from mining using the stolen resources, and quite likely a lot more. Since Wordfence reported the attack campaign on Monday, they report that the volume of the attacks has varied widely. This may indicate that the attacker is tweaking how they are allocating the stolen resources between attacking more sites and mining Monero. Yesterday they reported that the number of attacking IPs reached a new high, suggesting that the attacker’s botnet has the capacity to dial up their attacks on websites, but choosing to allocate more of their resources to cryptomining. Neither Sucuri or VaultPress (Automattic) have mentioned anything about this on their blogs as of this writing. My solution for this security issue is to use the free version of the iThemes Security plugin. I actually use the Pro version, but the free version does combat brute force attacks. There are other WordPress security solutions, such as Wordfence, Sucuri and VaultPress.
Backdoor in Catpcha Plugin
Matt Barry of Wordfence reported on December 19 that a backdoor was found in the Captcha plugin for WordPress, which had over 300,000 active installs as of that date. The plugin had been sold recently to an undisclosed party, who apparently added the backdoor for the sole purpose of placing cloaked backlinks on his users’ sites. These links basically have their transparency set to 0% so they are invisible to humans, much like keywords were added to pages with the same color as the background in the old days of SEO. These cloaked backlinks allow him/her to increase the page rank in SERPs (Search Engine Results Pages) for other websites since only web crawlers such as Googlebot can read them. The fix here? Remove the Captcha plugin IMMEDIATELY.
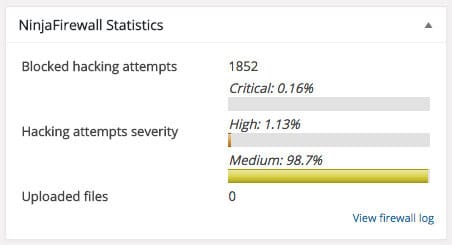
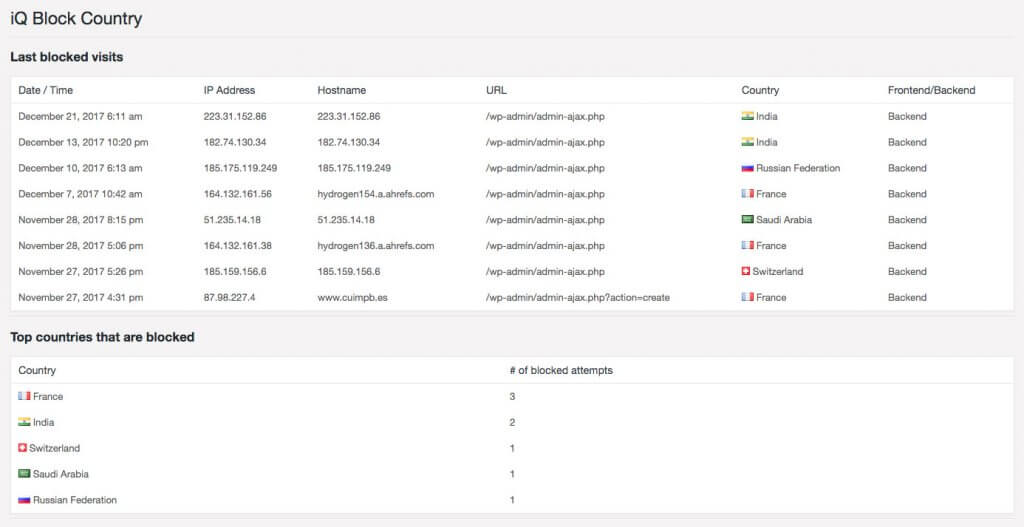
So, what can you do if you’re on a budget? 1) Install iThemes Security, 2) install iQ Block Country (you’ll need SFTP access to your site) and 3) install and configure the free version of the NinjaFirewall plugin. NinjaFirewall is set up in front of your WordPress site to block hackers and keeps the load on iThemes Security fairly low. iQ Block Country often takes out what’s left.